Subtotal $0.00
Enhancing SIEM Governance: Overcoming Key Challenges
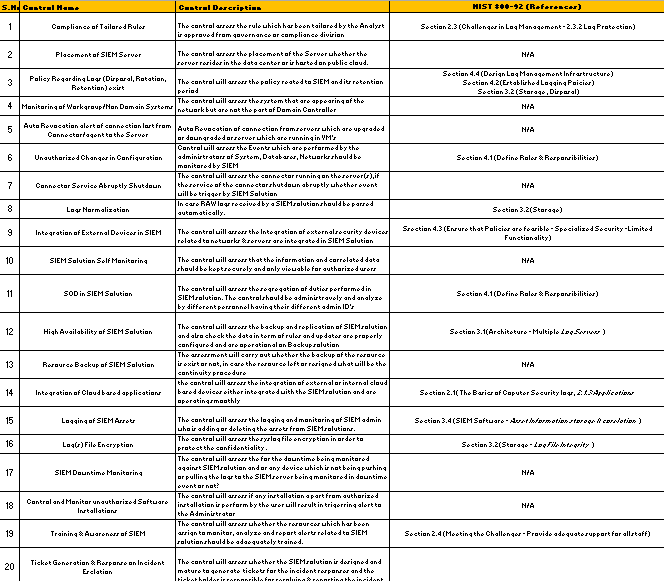
In the rapidly evolving landscape of cybersecurity, Security Information and Event Management (SIEM) systems play a pivotal role in detecting and mitigating threats. However, deploying and managing SIEM systems is not without challenges. Below, we explore key obstacles and how organizations can address them to ensure robust SIEM governance.
Compliance of Tailored Rules
One of the significant challenges is ensuring compliance with tailored rules. These customized rules are essential for meeting organizational requirements but can be complex to implement and maintain. According to Section 2.3 of NIST 800-92, organizations need to regularly review and update these rules to align with evolving security needs. Regular audits and fine-tuning are critical to achieving compliance and maintaining effective threat detection.
Placement of the SIEM Server
The strategic placement of the SIEM server within the network infrastructure is crucial for optimal performance. Poor placement can lead to latency issues and hinder real-time threat detection. Organizations must evaluate their network topology and place the SIEM server in a location that ensures seamless data flow and accessibility without compromising security.
Policy for Log Management
Log management is a cornerstone of SIEM operations. Policies for log disposal, rotation, and retention must adhere to best practices outlined in Section 4.4 of NIST 800-92. Inadequate log management can result in non-compliance and operational inefficiencies. Organizations should implement automated tools and clearly defined policies to streamline log management processes and ensure adherence to regulatory requirements.
Monitoring Workgroup and Non-Domain Systems
Another significant challenge is monitoring workgroup or non-domain systems, which are often overlooked in traditional SIEM setups. These systems can introduce blind spots into the organization’s security posture. To address this, organizations should implement mechanisms to integrate and monitor such systems effectively, ensuring no part of the infrastructure is left unprotected.
Auto-Revocation Alerts for Lost Connections
Maintaining active connections between servers and the SIEM system is critical. Auto-revocation alerts for connection losses help mitigate risks associated with compromised or inaccessible servers. By automating this process, organizations can promptly identify and resolve issues, minimizing downtime and potential vulnerabilities.
Conclusion
Effective SIEM governance requires addressing these challenges through a combination of strategic planning, robust policies, and adherence to industry standards like NIST 800-92. By doing so, organizations can optimize their SIEM systems to enhance threat detection, ensure compliance, and protect their infrastructure from ever-evolving cyber threats.

Comments are closed