Subtotal $0.00
Comprehensive Analysis of Cybersecurity KPIs:
Cybersecurity remains a cornerstone of organizational resilience in the face of evolving digital threats. The metrics from the provided data file shed light on three critical areas of focus: Threats, Incident Management, and Risk Management. This article delves into the specific findings and their implications for enhancing cybersecurity readiness.
Threats KPI: Key Metrics and Observations
The Threats KPI sheet provides a quantitative snapshot of an organization’s threat landscape:
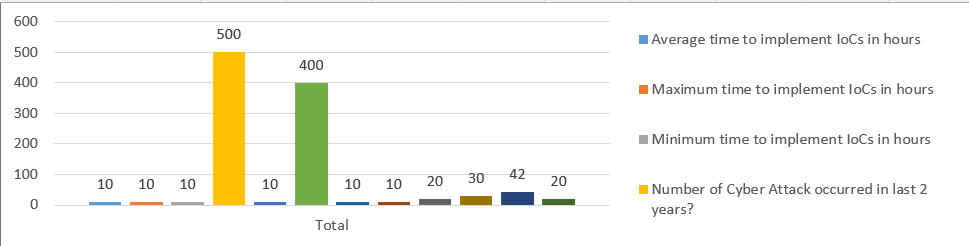
- Cyber Threat Intelligence Units (CTI-U): Organizations maintain 10 active CTI-U, highlighting a strategic focus on centralized threat monitoring and analysis.
- Cyber-Attack Incidents: Over the last two years, 500 cyber-attacks were reported. This statistic underscores the persistent and widespread nature of cyber threats that organizations face daily.
- Threat Intelligence Sources: With 20 subscribed intelligence sources, organizations are leveraging diverse data streams to gather actionable insights.
- Threat Information: A total of 30 general and 42 specific pieces of threat-related information were received, reflecting the emphasis on actionable intelligence tailored to unique organizational needs.
These metrics emphasize the importance of proactive intelligence gathering and analysis as foundational pillars of cybersecurity defense.
Incident Management: Policy, Response, and Testing
The Incident Management sheet outlines key aspects of an organization’s preparedness and response to cybersecurity incidents:
- Incident Management Plan: While organizations have developed and approved cybersecurity incident management plans, it is critical to regularly review and update these plans to address emerging challenges.
- Incident Response Teams: The existence of dedicated cybersecurity incident response teams ensures a prompt and coordinated reaction to potential breaches.
- Communication Plan: An approved communication plan for cybersecurity incidents is vital for effective stakeholder engagement and mitigation efforts.
- Testing Protocols: Regular testing and drills of the incident response plan are essential to identify gaps and improve the effectiveness of the strategy. However, the details of recent tests or revisions are not specified.
These metrics highlight areas where organizations must focus on continuous improvement to ensure a state of readiness for incident response.
Risk Management: Addressing High-Risk Observations
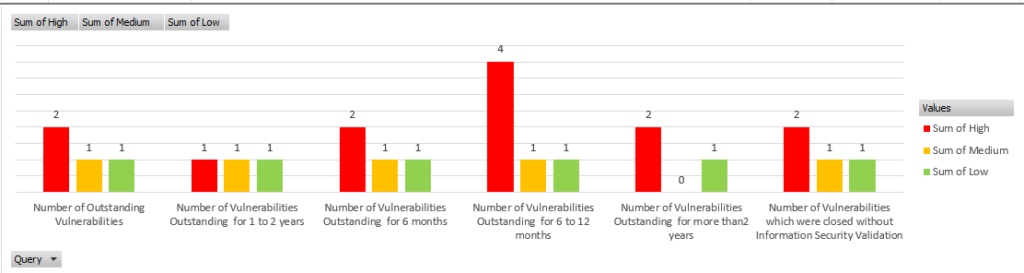
The Risk Management sheet captures the organization’s approach to high-risk observations:
- Untreated or Overdue Risks: Metrics on the number of untreated high risks and overdue risks provide insight into potential vulnerabilities. Addressing these issues promptly is critical to minimizing exposure.
- Categorization and Prioritization: Effective classification of high risks enables better resource allocation and prioritization of mitigation efforts.
By focusing on these metrics, organizations can strengthen their overall risk management framework, reducing their vulnerability to high-priority threats.
Recommendations and Conclusion
From the insights provided, it is evident that organizations are making strides in threat intelligence, incident management, and risk mitigation. However, there are clear opportunities for improvement:
- Enhanced Threat Monitoring: Expand the scope of threat intelligence sources and ensure timely action on specific threat information.
- Regular Plan Updates: Continuously update incident management and communication plans to reflect the latest threat landscape.
- Testing and Drills: Conduct regular incident response testing to identify and address weaknesses in protocols.
- Risk Prioritization: Address untreated and overdue high risks promptly to strengthen the overall security posture.
A comprehensive approach combining these elements can significantly bolster an organization’s defense mechanisms, ensuring resilience against ever-evolving cyber threats

Comments are closed