Subtotal $0.00
DIGITAL / CYBER FORENSIC & COMPROMISE ASSESSMENT
Rapidiously repurpose leading edge growth strategies with just in time web readiness service Objectively communicate timely meta services for synergistic initiatives functionalities.
Workshop Objective
• Understand the need of compromise assessment
• Gain visibility of malicious activity, identify and
confirm the breach.
• Develop ability to foresee and assess upcoming
cyber challenges
• Collect evidence for an effective response with law
enforcement, partners and customers.
• Improve internal capacity for incident detection,
containment & mitigation
Introduction to Cyber Forensic
Demonstration of Email Spoofing
Cyber Investigation Against Mobile Devices
Next Gen Cyber Blunders by Experts
Advance Level compromise assessment
Role of an Individual during compromise assessment
Demonstrating a scenario of compromise assessment
Demonstration to find attacks who are currently in the
environment or had been active
INTRODUCTION TO CYBER FORENSIC
Cyber forensics, e-discovery (electronic evidence discovery), digital forensics, computer forensics, all relevant,
each meaning relatively the same thing, and depending on whom you speak with, each meaning something very
different, yet none has emerged as a de facto standard.
The term specifically used for collecting, examining, Analyzing & reporting of data from the device.
INTRODUCTION TO COMPROMISE ASSESSMENT
Compromise assessment is a proactive approach for evaluation of systems to detect threat that have evaded
existing controls.
A compromise can be defined in three states:
• Applications – Applications become one of the weakest link in compromise the systems, lack of application
level security controls may lead towards compromise. For e.g.(SQL, Apache, IIS, torrent, WinRAR, Acrobat) etc.
• Operating System – Operating systems are another way of compromising the accessibility of the system by
triggering up a OS level vulnerability. For e.g. (Windows, Linux, Solaris) etc.
• Network – Networks connects applications and operating system by means of IP addresses and ports
numbers. Network side become vulnerable if not properly organized by a known professional which may leads
towards compromise state. Network attacks which may leads towards compromise are included but not
limited to ARP Spoofing, DNS Spoofing, IP Flooding, IP Spoofing, DHCP Starvation) etc
EMAIL SPOOFING
Email spoofing is a popular tactic used in phishing and spam campaigns because people are more likely to open
an email when they think it has been sent by a legitimate or familiar source. The goal of email spoofing is to get
recipients to open and reply to the email seems urgent in by its content and requires some financial or
confidential data from the user.
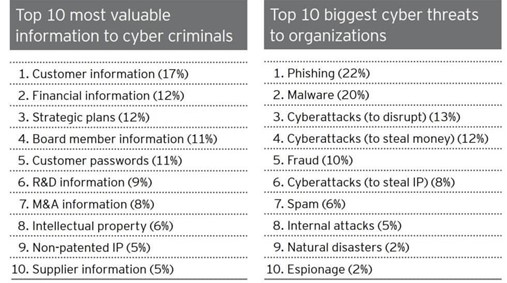
According to the survey conducted by E&Y the statistics shows that 22% of the attacks comes by running a
phishing campaign against the organization.
Email spoofing is a popular tactic used in phishing and spam campaigns because people are more likely to open
an email when they think it has been sent by a legitimate or familiar source. The goal of email spoofing is to get
recipients to open and reply to the email seems urgent in by its content and requires some financial or
confidential data from the user.
EMAIL SPOOFING PREVENTION
A spoofed email message is modified to appear as if it originates from a sender other than the actual sender of
the message. To stop email spoofing, following are the key step which requires special considering when securing
from email spoofing.
Reference.: https://www.comparitech.com/vpn/cybersecurity-cyber-crime-statistics-facts-trends/
Using Sender ID to counter from spoofing attack;
Creating Sender Policy Framework (SPF) record entry: Sender Policy Framework – or SPF as it is commonly known
– is a solution created in an attempt to validate the source of an email message received by a mail system.
SPF policies work by adding a TXT record to your email domain’s DNS (domain name server) that identifies the
authorized mail servers for sending email for this domain
An example record:
v=spf1 include:mail.example.com -allA spoofed email message is modified to appear as if it originates from a sender other than the actual sender of
the message. To stop email spoofing, following are the key step which requires special considering when securing
from email spoofing.
Configuring Domain Message Authentication Reporting and Conformance (DMARK) record – DMARC not only
advises the receipt to quarantine or reject the email message on failure, but also asks for a report of the message
to be sent to a reporting address. This is a great step for gaining some insight into spam/malspam campaigns
spoofing your organization.
An example record:
V=DMARC1; p=none; rua=mailto:report.rua@example.com;
ruf=mailto:report.ruf@example.com A spoofed email message is modified to appear as if it originates from a sender other than the actual sender of
the message. To stop email spoofing, following are the key step which requires special considering when securing
from email spoofing.
Domain Keys Identified Mail (DKIM) – DKIM this is used to publish the signer’s public key, which the recipient mail
server then uses to verify that the content signed by the digital signature is included in the email message
headers.
An example DKIM record:
V=DKIM1; k=rsa; p=PUBLICKEY
CYBER INVESTIGATIONS AGAINST MOBILE DEVICES
Mobile device is become one of key threat which user is are carrying with them. Its not like a hand grenade but it
is not less then a hand grenade the difference is that a hand grenade can physically harm and this threat can
logically harm user by stealing the privacy of the users data.
Cybercriminals targeting mobile devices most frequently use apps to break in, as seen in 79% of mobile-focused
attacks in 2019 and 76% of those in 2020 so far, Pradeo Labs researchers found MOBILE PHONE USERS STATISTICS IN PAKSITAN
According to the latest stats of Pakistani market, 94.61% are using android based cell phone devices, 3.74% are
using iOS devices.
|
Date |
Android |
iOS |
Nokia Unknown |
Series 40 |
Unknown |
Windows |
Symbian OS |
Samsung |
BlackBerry OS |
Linux |
Other |
|
2019-11 |
95.21 |
3.06 |
0.9 |
0.27 |
0.16 |
0.21 |
0.08 |
0.04 |
0.03 |
0.02 |
0.02 |
|
2019-12 |
95.11 |
3.25 |
0.85 |
0.24 |
0.16 |
0.19 |
0.07 |
0.04 |
0.03 |
0.02 |
0.02 |
|
2020-01 |
94.61 |
3.74 |
0.85 |
0.24 |
0.15 |
0.21 |
0.07 |
0.06 |
0.03 |
0.02 |
0.02 |
Reference: http://gs.statcounter.com/os-market-share/mobile/pakistan
MOBILE ATTACK DEMONSTRATION
Binding malware with a legitimate
application hosted over various
open market places.
Malicious App Contains:
Reverse Back
Connection
Intruder IP
Intruder Port
Malicious App Will Intrude:
SMS (Dump, Send/Receive)
Call Log
Gallery
Live Camera
Microphone, Contact Directory,
Location Tracking etc.
NEXT GEN CYBER BLUNDERS BY EXPERTS
Implementing the security controls is not the only solution for enhancing organization from the security point of
view, there are several tuning which may require to be implemented by the experts of those system which may
include but not limited to:
If we discuss about security solution, the ideal scenario for all the organization providing critical services would be
as follow:
1. An endpoint solution is implemented through out the organization;
2. A Security Incident & Event Management solution (SIEM) is implemented to monitor critical server(s) and
applications;
3. Intelligent Firewall for network traffic monitoring;
4. SPAM filter for controlling SPAMMING and SPAMMERS;
SIEM SOLUTION: Securing organization by pushing up a notification of suspicious event in order to preventing
from data breaches.
I would like to add one thing whether your SIEM solution is capable for monitoring such event or not?
S. No Event Name Event Description Event I
|
S. No |
Event Name |
Event Description |
Event ID |
|
|
|
RANSOMWARE |
|
|
1 |
Object Access |
An attempt was made to access a file |
4663 |
|
2 |
Sensitive Privilege Use |
When user exercise privileges assign to them |
4673 |
|
3 |
Process Creation |
A process is create when a process is created |
4688 |
|
4 |
Process Termination |
A process is terminate when a process is terminated |
6889 |
|
5 |
Process Special Logon |
Special privileges assign to new logon |
4672 |
|
|
|
TROJAN |
|
|
6 |
Trojan Detected |
Indicates that Trojan was detected |
6008 |
|
7 |
Service Control Manager |
The Windows Defender Services entered the stopped state |
7036 |
|
8 |
Remote Access |
Indicate that backdoor was created |
6002 |
|
9 |
Sending E-mail |
Hostile Email was attached |
6003 |
|
S. No |
Event Name |
Event Description |
Event ID |
|
|
|
WORMS |
|
|
10 |
Service Installed |
An unknown service was installed in the system |
4697 |
|
11 |
File Share |
A network object was accessed |
5140 |
|
12 |
File Share |
A network object was added |
5142 |
|
13 |
Bootnet DNS interception |
Redirect the traffic to malicious site |
338301 |
|
14 |
Bootnet Destination blacklist |
Access to malicious site |
338004 |
|
VIRUS |
|
||
|
15 |
Malicious software |
Indicates a virus |
6004 |
|
16 |
Content scan |
An attampt was made to scan the content present in system |
6010 |
|
17 |
Disk-Bad block |
Area of storage that is no longer reliable for storing and retriving data |
7 |
|
18 |
Disk-Disk error during paging |
Error occurs when your computer swaps information to or from the disk. |
51 |
|
19 |
Disk-imminent disk failure |
Hard drive failure |
52 |
|
20 |
Application Error |
An attempt was made to crash the application |
1000 |
|
SPYWARE |
|
||
|
21 |
Spyware Detected |
Indicates a spyware was detected |
6009 |
|
22 |
Service Control Manager |
Indicates a new service local synchronization host was installed |
7045 |
|
23 |
Service control Manger |
Indicates local synchronization host service entered the running state |
7036 |
|
24 |
System Logon |
Logon session was created to logon to local computer |
4624 |
|
25 |
User Account Mangement |
An attempt was made to reset the account’s password |
4724 |
|
|
|
ADWARES |
|
|
26 |
Software Install |
Indicates that software was installed |
11707 |
|
27 |
Software Uninstall |
Indicates that software was uninstalled |
11724 |
|
|
|
ADORE ROOTKIT |
|
|
28 |
object Access Request |
When an application attempt to access the obejct |
4656 |
|
29 |
Changed Object Permission |
Someone made changes to access control list of object |
4670 |
|
30 |
Object Access |
An attempt was made to access any object like kernel |
4663 |
|
|
|
HACKER DEFENDER ROOTKIT |
|
|
31 |
Process Create |
A new process has been created |
4688 |
|
32 |
Registry |
Registry valued was modified |
4657 |
|
33 |
Application Error |
An attempt was made to crash the application |
1000 |
|
|
|
STONED BOOTKIT |
|
|
34 |
Service Control manager |
The Protected Storage service failed to start due to the following error: The system cannot find the path specified. |
7000 |
|
35 |
Active Directory Doamin Service |
An internal asynchronous attempt to update the schema cache failed with an error. |
1208 |
|
36 |
System -Drives |
The Boot-Start or System-Drives are failed to load |
7026 |
|
|
|
DNS CHANGER EXPLOIT KIT |
|
|
37 |
Remote Access |
Remote Desktop Services accepted a connection from IP address |
1158 |
|
38 |
DNS |
an attempt was made to update them with the new records through dynamic update |
6702 |
|
39 |
Application |
C:\Program Files\Microsoft Silverlight\slup.exe cannot be restarted |
10010 |
COMPROMISE ASSESSMENT CHECKLIST
|
S. No |
Control Name |
|
Objective |
Technique |
Status |
||
|
Yes |
No |
||||||
|
|
|
Compromise Assessment Checklist – System/Server |
|
|
|
||
|
1 |
|
User Access Control |
Assessing the User Access Privilege rights for the OS. |
Review of Access right form |
|
|
|
|
2 |
|
Searching for Cracked OS |
Assessment of OS by examining its serial no. |
Product key viewer/ key finder |
|
|
|
|
|
|
Searching for Outdated, Obsoleted, End of Life OS |
Assessing OS version and Firmware, release issued officially by the vendor |
Winver (Windows) uname -a (Linux) |
|
|
|
|
3 |
|
Anti Virus/End point/Defender real time protection |
Ensure that the AV/End points real time protection is turned on |
Manual technique |
|
|
|
|
4 |
|
AV/Endpoint/OS Updates |
Ensure that the AV/End points are Up to dated. |
Manual technique |
|
|
|
|
5 |
|
Cracked tools |
Assessment of any cracked tool installation (MS Office, Acrobat, IDM, etc.) |
Examining installed programs |
|
|
|
|
6 |
|
Open Source tools |
Assessment of any open source tool installation (Firefox, VLC, VEEAM, Chrome etc.) |
Manual technique |
|
|
|
|
7 |
|
Browser Plug-ins |
Assessment of Installed plug-ins in the browser ( Video Downloader, File Converter etc.) |
Manual technique |
|
|
|
|
8 |
|
Application Activity Monitoring |
Assessment of activity performs by examining processes of the application(s) |
Process Monitor Apps (procmon, ps -a) Wireshark |
|
|
|
|
S. No |
Control Name |
|
Objective |
Technique |
Status |
||
|
Yes |
No |
||||||
|
|
|
Compromise Assessment Checklist – System/Server |
|
|
|
||
|
9 |
|
Email/USB Attachments |
Assessment of malwares, Trojans, Macros attached in email/USB attachments transferred in the system. |
|
|
|
|
|
10 |
|
Key logger |
Assessment of Malwares, key logger/Spying tools and Trojans . |
Manual technique |
|
|
|
|
11 |
|
Java Auto Run |
Reviewing installation of java in the system in order to assess auto execution capability of java applets, scripts, java runtime environment files |
Manual technique |
|
|
|
|
12 |
|
Shells |
Searching for connections (Listening, Established) |
netstat -a, netstat -bano (Windows) ss -tulw, ss-tulwn (linux) |
|
|
|
|
13 |
|
Unnecessary Port Assessment |
Searching for unnecessary ports opened on the server |
netstat, NMAP |
|
|
|
|
14 |
|
Searching for Stored Credentials |
Searching for Stored Credential in Windows, Browsers, Applications |
rundll32.exe keymgr.dll,KRshowKeyMgr |
|
|
|
|
15 |
|
Network Monitoring |
Assess Network Behavior |
Nmon |
|
|
|


Comments are closed